A cyber-attack took place on the weekend days falling before the 14th of Sep. What seems to be the largest hacking attack similar to a Magecart, it had injected malicious code in the source code of almost 3000 Magento sites that logged the payment information of customers. It is speculated that the majority of those stores were running on End-of-Life version Magento 1. Security researchers at Sensec have termed this largest campaign ever as a CardBleed.
What is CardBleed?
CardBleed is a massive automated hacking attack that took place on almost 3000 Magento stores executed in September 2020. The code name CardBleed was coined by Sensec to differentiate it from other campaigns. As per the experts at Sensec, CardBleed is by far the biggest automated cyber hacking attack identified since 2015. The previous record for the same is 962 in a single day, which was executed last year in July.
How Did This Happen?
Several experts from the web security community found no new Magento 1.X vulnerability, which was uncharacteristic as it was the old version riddled with security holes. At that time, security experts believed that hackers were sitting duck intentionally waiting for Magento 1.X to come to EOL.
Turns out, the experts were right. Hackers made sure that Adobe didn’t patch the old Magento 1 version and then started exploiting them with malicious code injection.
The incident first came to light on Monday, 14th of Sep 2020 by Sensec’s early breach detection system. It is a global eCommerce monitoring system, which detected that a total of 1904 Magento stores were hacked through a new and unique keylogger skimmer over that weekend. And to date, over 2800 (almost 3% of Magento 1 installs) Magento 1 stores are infected by this Magecart like skimming attack.
This means that the payment and other information of customers with those Magento stores have been compromised. Also, it identified that mostly those Magento stores were running on now deprecated EOL Magento 1.X. This kind of attack was anticipated from the last year even before the Magento 1 reached its official End-of-Life date.
Adobe – the owner of Magento – has been warning store owners about this plausible scenario because of the increasing number of web skimming (Magecart) attacks. Not only that but payment processors like PayPal, Visa, and Mastercard had also warned Magento store owners of the same.
Warnings by Adobe, PayPal, Visa, and Mastercard
Adobe has given a warning to its merchants about the EOL of Magento 1 and suggested the possible solution as a total migration to Magento 2. This was intended to make the online Magento stores safer, secure, and sound from all the malicious and skimming attacks.
Similar warnings have been given by the payment processors like PayPal, Visa, and Mastercard all of which also suggested migrating on a newer platform to stay compliant with PCI DSS guidelines. All these payment processors have indicated the potential security risks of staying with Magento 1 after its End-of-Life.
Also, a few months before the official EOL date, we have explored the thing that could happen if you continue to use Magento 1 after EOL. We explicitly explained the life of a Magento 1 store owner after June 30th. And one likely scenario was going through this kind of attack. It was not only us, but many experts suggested the same.
$5000 for Magento Exploits
Many Magento stores compromised by this CardBleed attack have no prior history of going through such security incidents. This means that a new skimming method was used by the hackers to gain server access to stores running on Magento 1. Experts at Sensec doubt that this largest skimming attack may be related to the Magento 1 0day (exploit) that was put up for sale on an underground hacking forum.
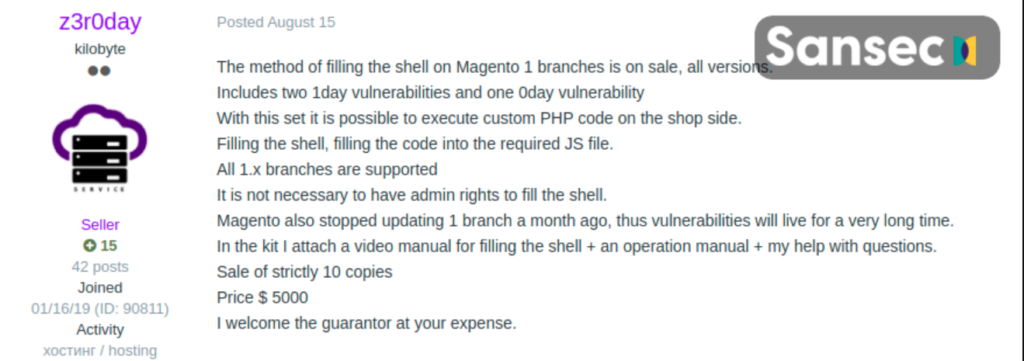
A user named z3roday on a hacking platform was found to sell remote code execution exploit method along with a video attached showing the intrusion all for $5000. He stressed that no patches are provided by Magento for the EOL branch, which will help exploit the stores on a legacy platform with extra damage and for a longer time.
95000+ Magento Stores are at Risk
As per official data, there are still more than 95000 stores running on the EOL version of Magento. This number is reduced from a whopping 240,000 from last year. It’s believed that most of these stores are abandoned or generate low traffic. Still, there are a few stores with a high volume of traffic running on Magento 1.x and are relying on the Web Application Firewalls (WAFs) to stop these kinds of attacks.
This strategy may allow you to bypass the PCI guideline and make your store PCI compliant but in the long run, it’s not an effective solution.
How To Save Your Magento 1.X Store?
The only possible solution to stay safe from such kind of incidents is Magento 1 to Magento 2 Migration Service. If you are a store owner running on the older version of Magento even after EOL, then you are at a high risk of getting skimmed or hacked at any time. Because there is no official support from Adobe, and third-party patch support is not a long-term sufficient solution.
The only solution to save your Ecommerce store is to migrate it to the latest stable version of Magento 2. Because Magento 2 can better handle cross-site scripting and remote code execution and help you secure your Ecommerce store. The quarterly upgrades from Magento make sure that your Magento 2 store has capabilities to defend itself from such kind of attack by eliminating the possible vulnerabilities.
Also, in the first week of this month, Magento has announced a partnership with Sensec to integrate its security scan tool with the backend of Magento 2. This will allow Magento 2 Commerce and Commerce Cloud merchants to enhance the security of their storefronts.
So, all in all, Magento 2 is the future and only solution to save your online Ecommerce store from getting skimmed or hacked. If you still have doubts, then consult our experts to discuss it further. We have several experts and researchers who will provide you quality consultation on Magento 2 Migration.

















